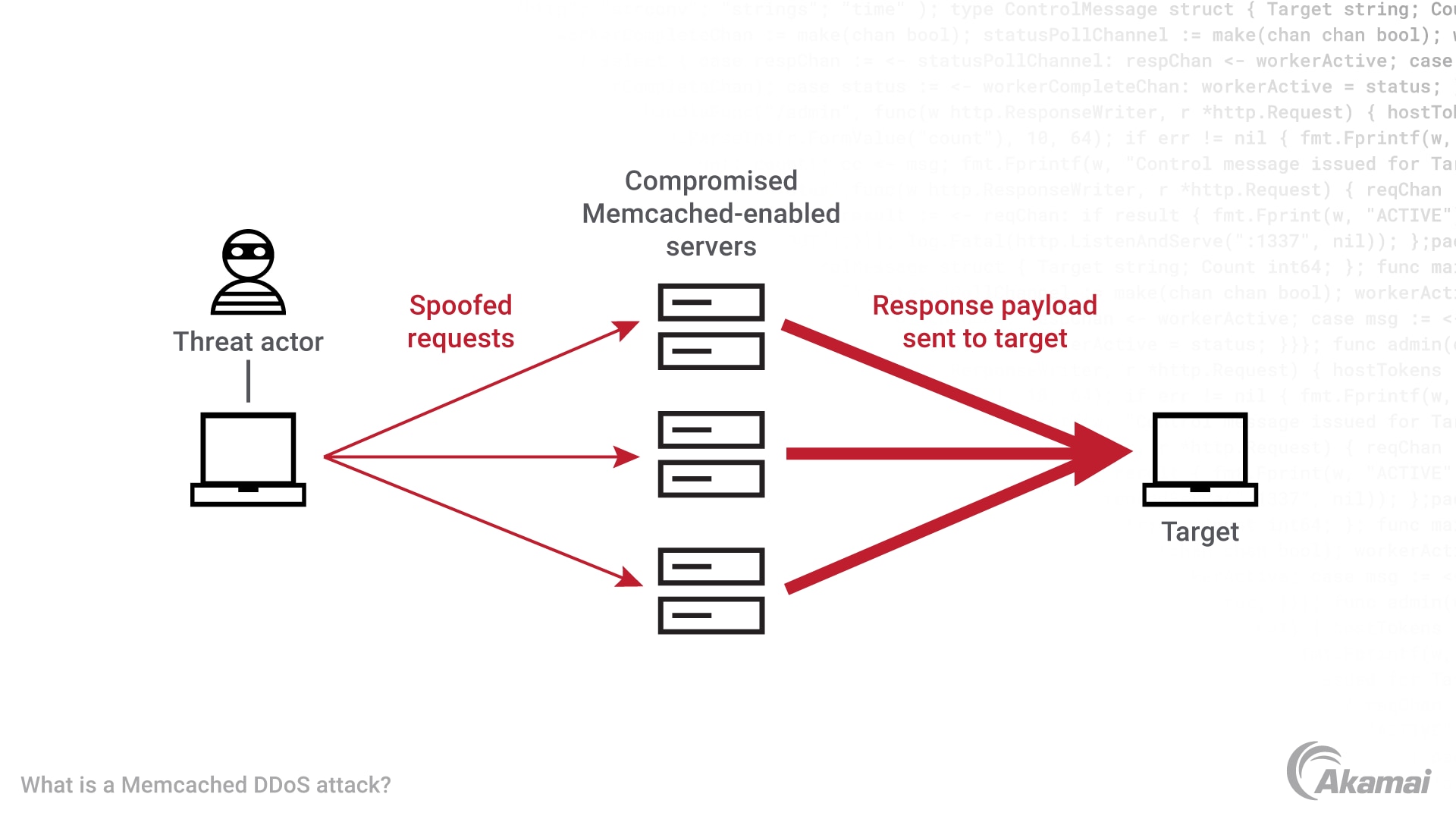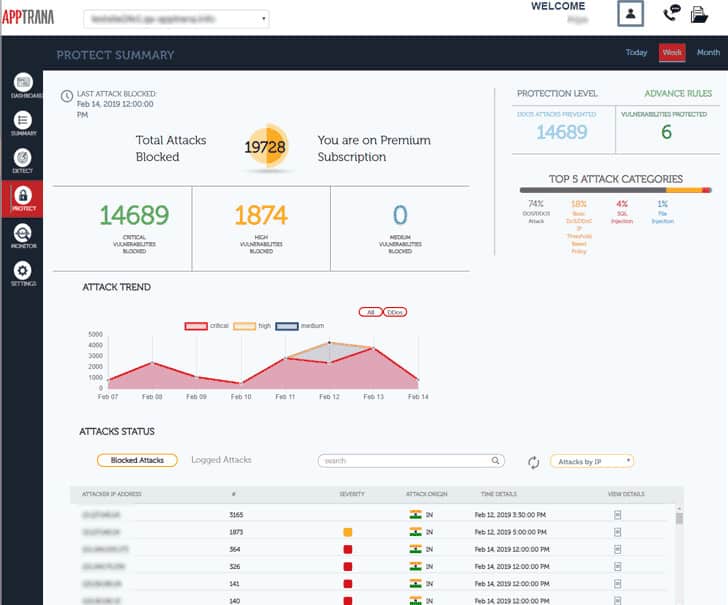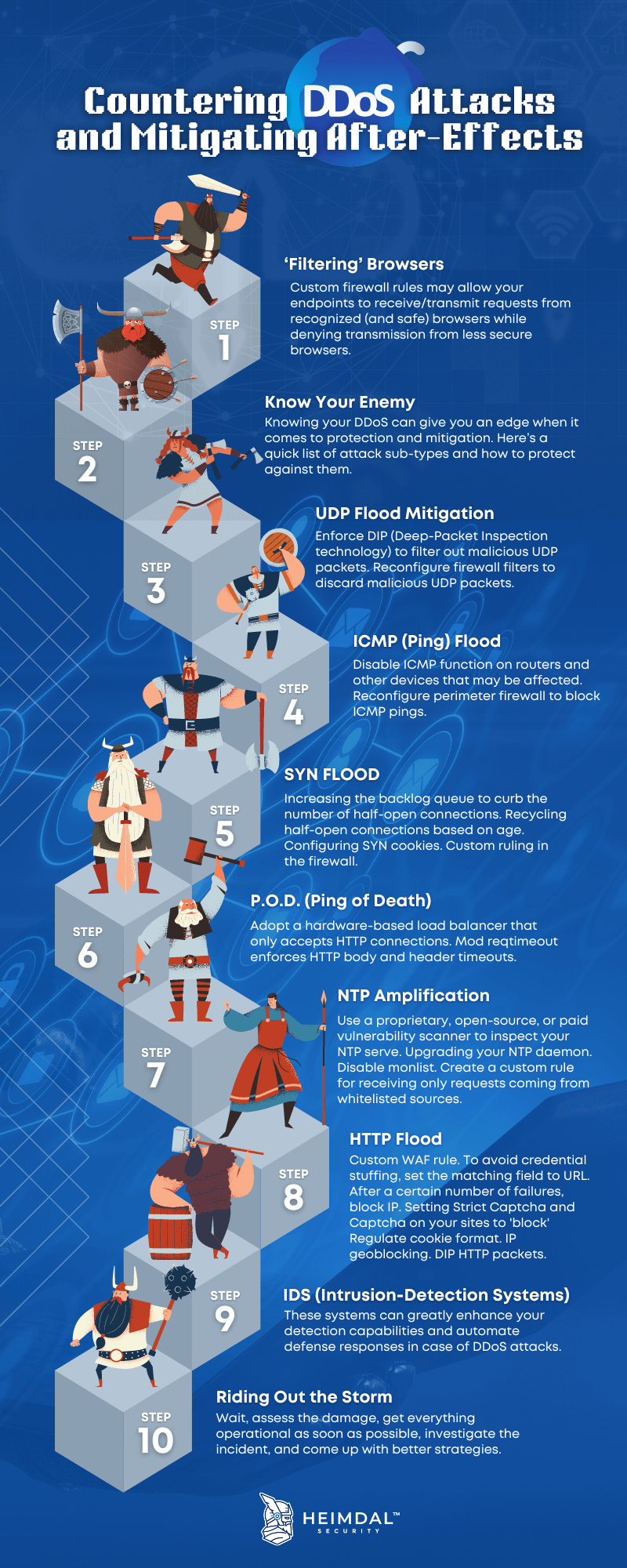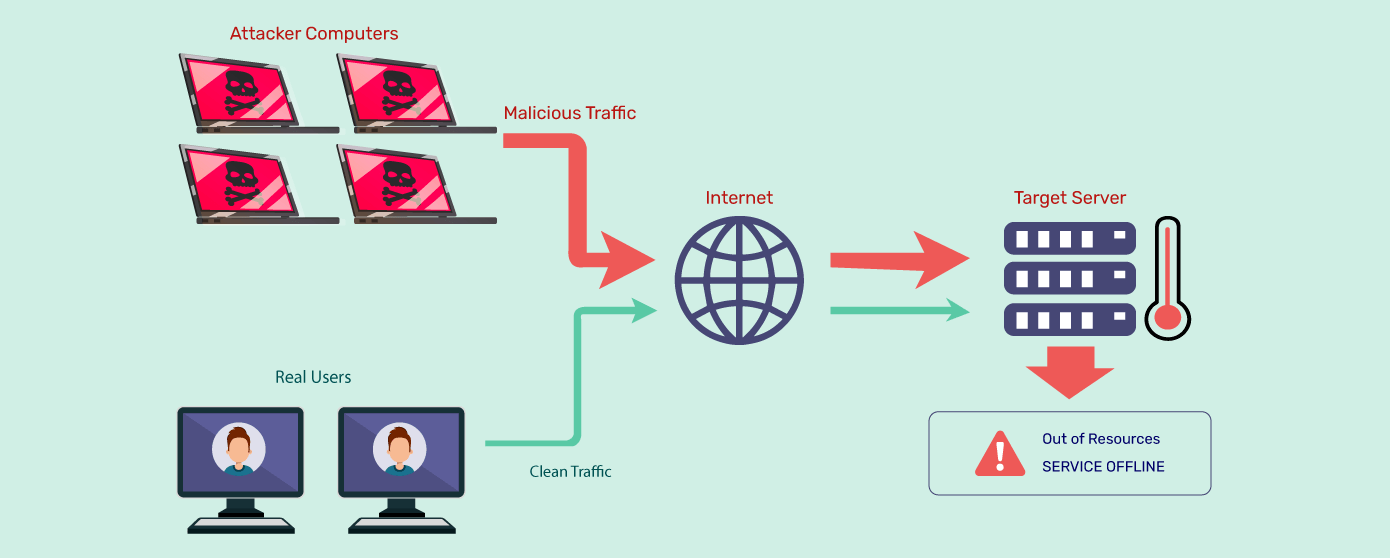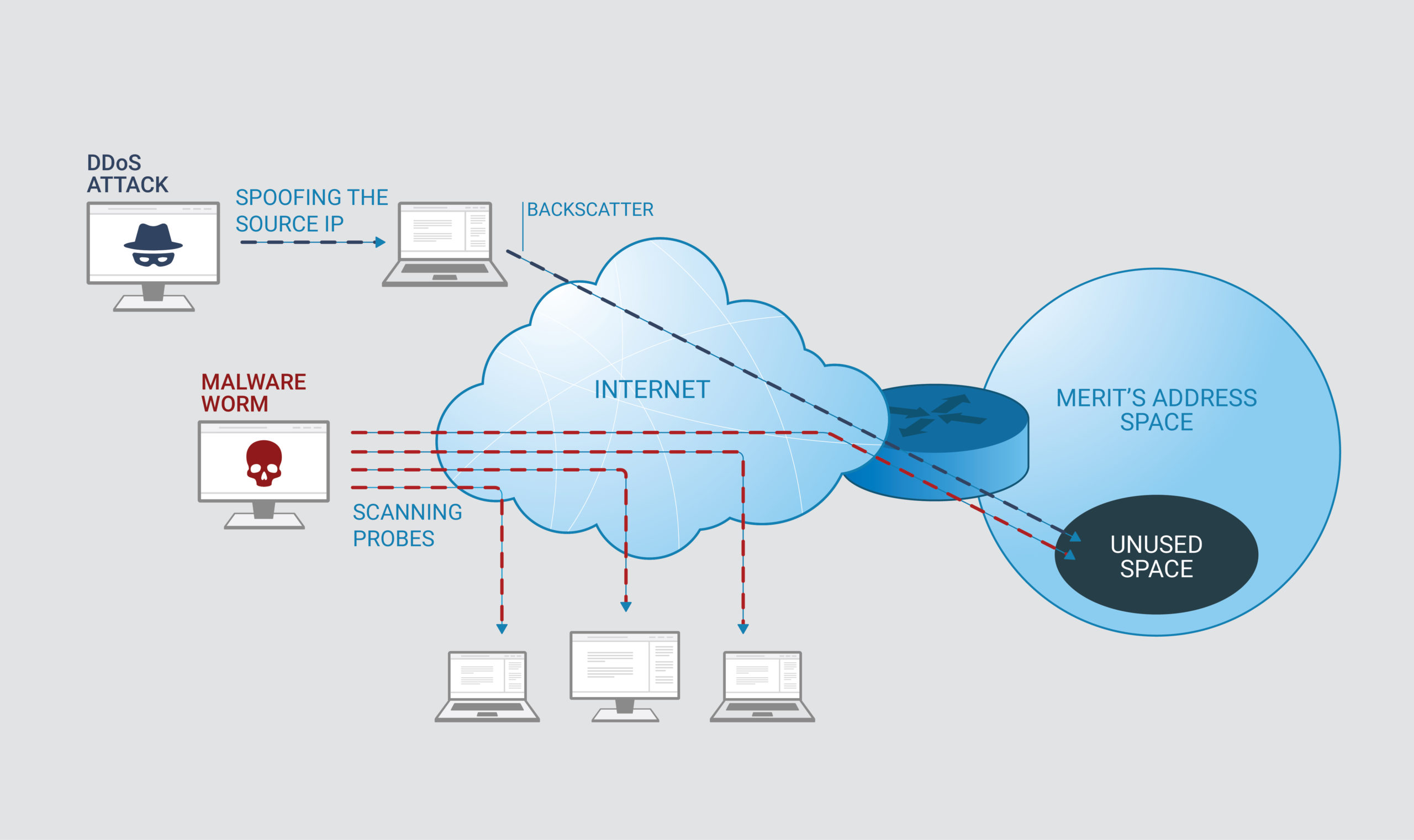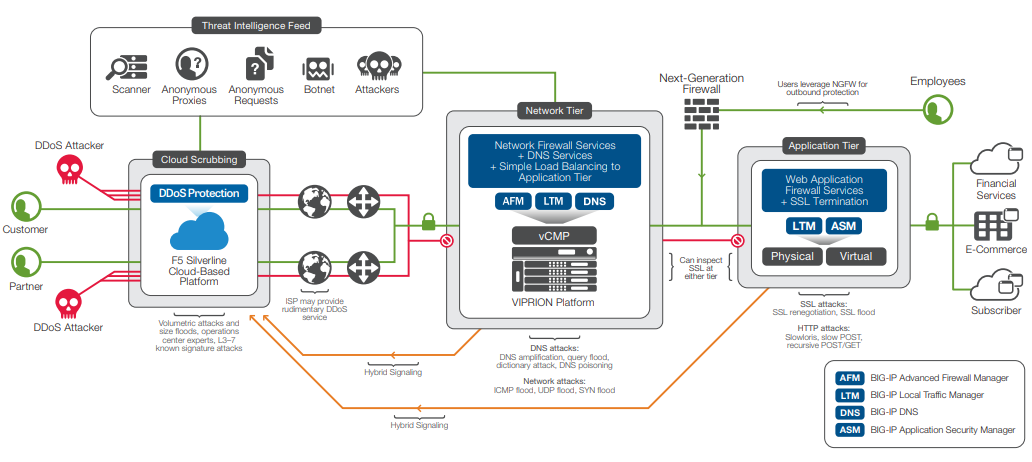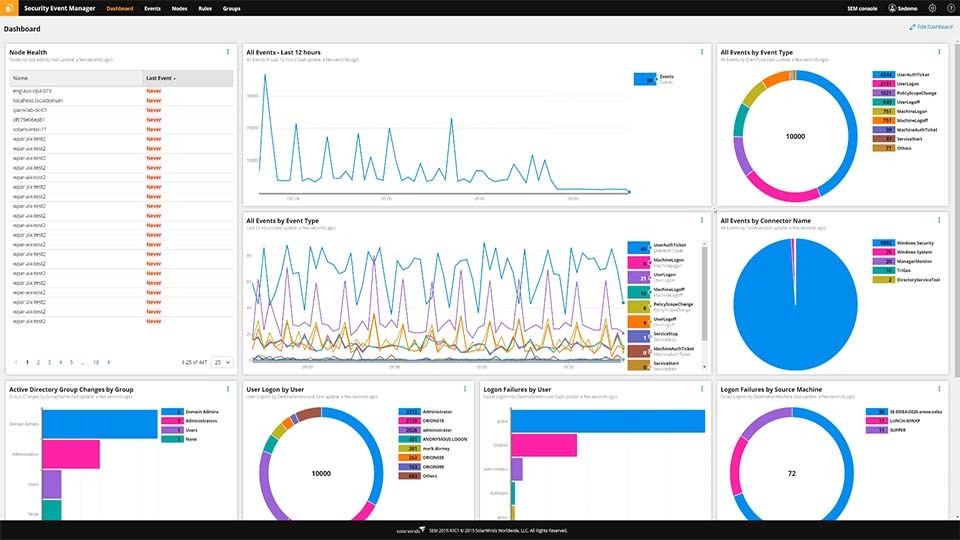
Applied Sciences | Free Full-Text | A Lightweight Model for DDoS Attack Detection Using Machine Learning Techniques
![PDF] Machine Learning Classification of Port Scanning and DDoS Attacks: A Comparative Analysis | Semantic Scholar PDF] Machine Learning Classification of Port Scanning and DDoS Attacks: A Comparative Analysis | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/4c304cfa88cd53cddd7f5547d9728737aa0988c7/2-Figure1-1.png)
PDF] Machine Learning Classification of Port Scanning and DDoS Attacks: A Comparative Analysis | Semantic Scholar

Free Course: Network Programming with Python Course (build a port scanner, mailing client, chat room, DDOS) from freeCodeCamp | Class Central
Premium Vector | Cyber security concept line icons set pack outline pictograms of fingerprint scanner spam ddos